Mar 12 2018
Using HTTPS on FarGate
This is the second post in a series on scaling the PDF Converter using Amazon’s FarGate service.
In the first post, we got the PDF Converter running across 2 instances behind a load balancer, in under 20 minutes.
Now, we want to use HTTPS. The Amazon documentation is at https://docs.aws.amazon.com/elasticloadbalancing/latest/application/create-https-listener.html
First, go to the AWS Certificate Manager (ACM): https://console.aws.amazon.com/acm/home?region=us-east-1#/firstrun/ to request a certificate (for your domain).
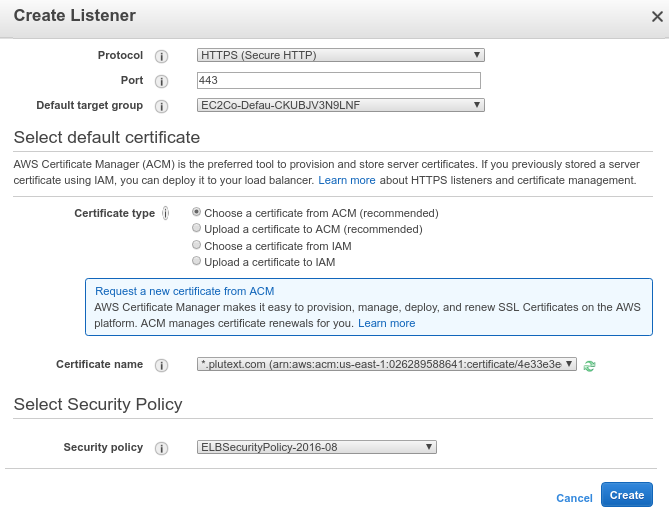
Now go to your load balancer, and choose “create listener“. Choose HTTPS. You should see something like:
(here I’ve used plutext.com, but obviously you’ll have substituted your own domain).
If/when you click “create”, you’ll probably get a warning saying your security group doesn’t allow HTTPS, so click on the security group to allow traffic on port 443.
We’re not quite there yet. If you try converting using your load balancer endpoint (something like https://EC2Co-EcsEl-1GY7BNHSDU1HTH-1150934046.us-east-1.elb.amazonaws.com:443), you’ll get an error saying the certificate subject name does not match target host name.
To overcome this, you need to update your DNS records so you have a host with the right name resolving to the load balancer.
The recommended way to do this is to use Amazon’s Route53 DNS.
But just to prove what we’ve done so far works, its enough to put an entry in your /etc/hosts file mapping a host covered by your certificate, to the load balancer’s IP address. Then:
$ curl -v -X POST --data-binary @HelloWorld.docx -o out.pdf https://fargate.plutext.com:443/v1/00
000000-0000-0000-0000-000000000000/convert
Note: Unnecessary use of -X or --request, POST is already inferred.
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0* Trying 54.89.45.53...
* Connected to fargate.plutext.com (54.89.45.53) port 443 (#0)
* found 148 certificates in /etc/ssl/certs/ca-certificates.crt
* found 597 certificates in /etc/ssl/certs
* ALPN, offering http/1.1
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0* SSL connection using TLS1.2 / ECDHE_RSA_AES_128_GCM_SHA256
* server certificate verification OK
* server certificate status verification SKIPPED
* common name: *.plutext.com (matched)
* server certificate expiration date OK
* server certificate activation date OK
* certificate public key: RSA
* certificate version: #3
* subject: CN=*.plutext.com
* start date: Mon, 12 Mar 2018 00:00:00 GMT
* expire date: Fri, 12 Apr 2019 12:00:00 GMT
* issuer: C=US,O=Amazon,OU=Server CA 1B,CN=Amazon
* compression: NULL
* ALPN, server accepted to use http/1.1
> POST /v1/00000000-0000-0000-0000-000000000000/convert HTTP/1.1
> Host: fargate.plutext.com
> User-Agent: curl/7.47.0
> Accept: */*
> Content-Length: 4082
> Content-Type: application/x-www-form-urlencoded
> Expect: 100-continue
>
< HTTP/1.1 100 Continue
0 4082 0 0 0 0 0 0 --:--:-- 0:00:01 --:--:-- 0} [4082 bytes data]
* We are completely uploaded and fine
< HTTP/1.1 200 OK
< Date: Mon, 12 Mar 2018 05:01:52 GMT
< Content-Type: application/pdf
< Content-Length: 38507
< Connection: keep-alive
< access-control-allow-origin: *
<
{ [16384 bytes data]
100 42589 100 38507 100 4082 16903 1791 0:00:02 0:00:02 --:--:-- 16903
* Connection #0 to host fargate.plutext.com left intact
Now we know it works, you can add a CNAME record at your DNS provider, mapping your chosen host name to the load balancer’s host name.
Remove the entry we added to /etc/hosts, give your CNAME entry time to propogate, then verify the curl command works.

No Responses so far
Comments are closed.
Comment RSS